
Since I started my journey with Hugo blogging platform migrating away from Wordpress several years ago I’ve been using Git more and more. It has been essential for me to save all critical work I am working on in Git. But as you are working it might happen that a secret or two might be pushed to the Git repository. I am not guilty of that but as my process of learning and mastering the technology I found out that there is a possibility to protect your Git repositories even before pushing anything to the repository. In todays post I will show you how easily it is to use GitGurardian and prevent secrets leaking to public repositories.
Luckily for us they provide free account with some nice stats.
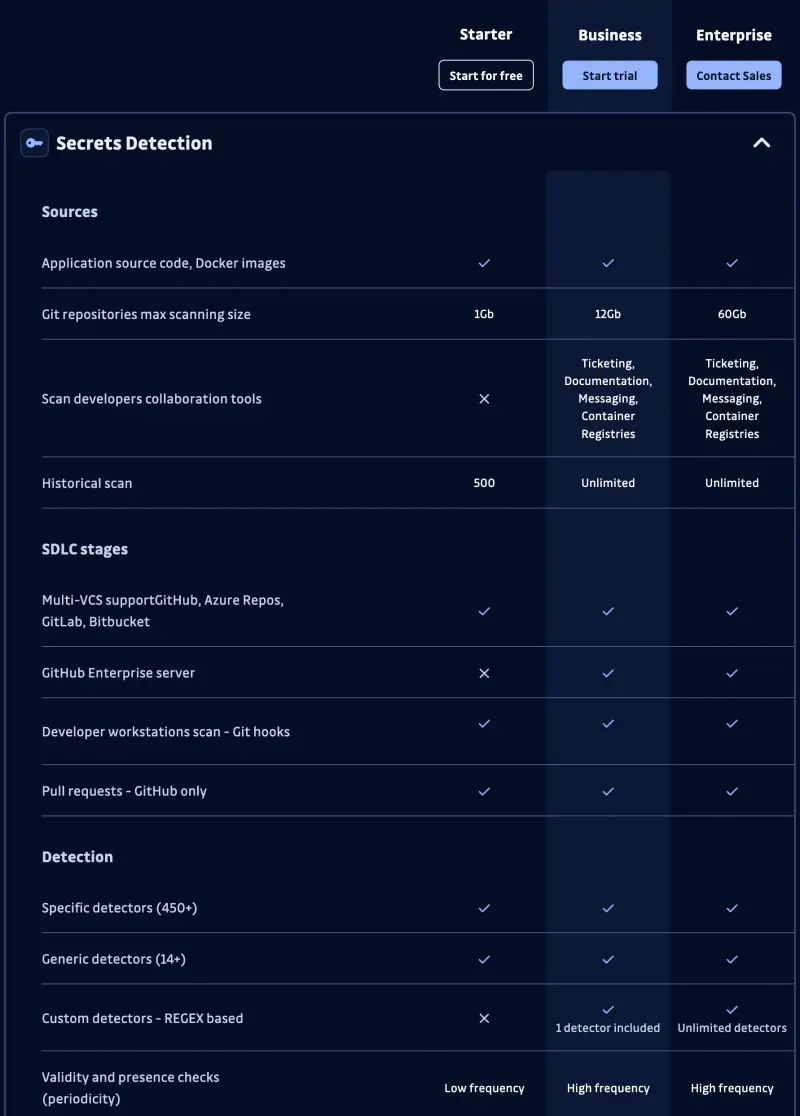
You can take a look at the detailed pricing.
Prerequisites
As a main prerequisite is Git repository. In my case I am using GitHub so I will show you how to configure it with GitHub.
ggshield installation
At first in your local environment you need to install ggshiled. It is a CLI tool which will will do the heavy work for you.
Simply follow your operating system installation guide.
Then you need to create GitGuardian account as you will need to authenticate via CLI.
Run manual repository scan
Now as we have ggshield CLI installed we can initiate our scan.
It is as simple as running the command ggshield secret scan repo /path/to/the/repo.
Here is the result of my manual scan on one of my repositories.
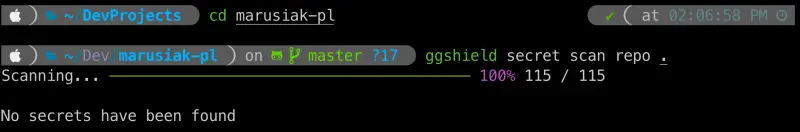
You can simply run this command on all of your repositories but if you have a lot of them it might take some time to do it.
Add pre commit hooks to secure your repository
It is possible to configure a pre commit hook in your Git repository so prior commit a ggshield CLI scann will be initiated.
In order to do it you need to create a file called .pre-commit-config.yaml. In tat file add following code
|
|
You can check if there are some changes in this code as per installation guide.
In order to add pre-commit we need to install it via Pip.
|
|
Once installed and the file is created you can simply by running command.
|
|
If installed successfully you will receive following output pre-commit installed at .git/hooks/pre-push.
After installing pre-commit before every push of code to Git repository it will be automatically scanned with ggshield.
If everything is configured correctly your repository should be scanned prior to push.
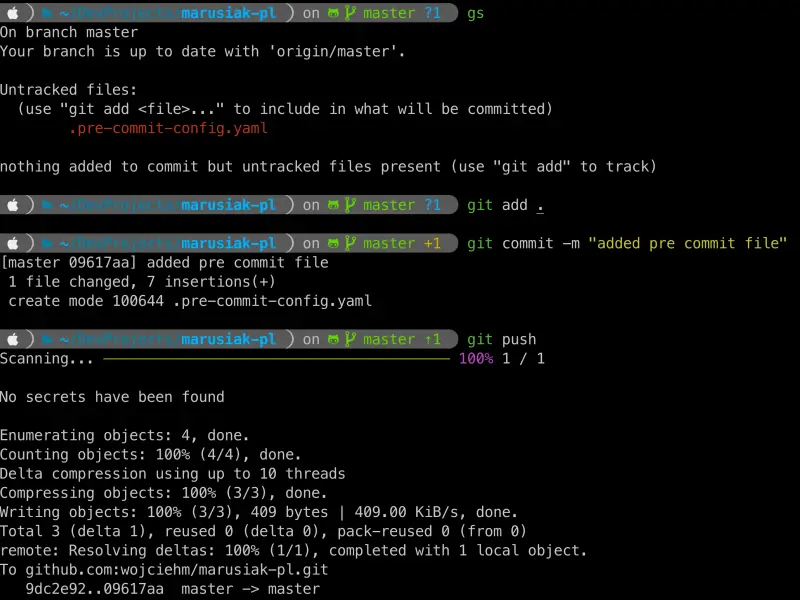
Optional - Scan all your repositories
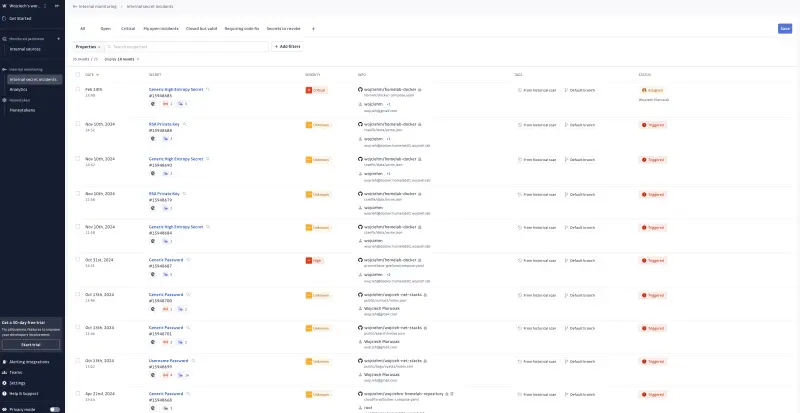
If you are ok with that you can grant GitGuardian permissions to scan your whole Git account. In my case I allowed this and several issues have been identified. Luckily for me all those affected repositories are private.
Summary
I hope you liked it and that this will help you to secure your Git repositories.