Today I faced quite a big challenge. I was working on setting up Grafana Alloy on my Ubuntu Server to ship logs to my Grafana instance. Pretty much all logs have been picked up but access to some logs have been blocked by AppArmor.
Bad AppArmor! A lot of sources in the Internet would simply disable it and problem fixed :)
Not on my server :D
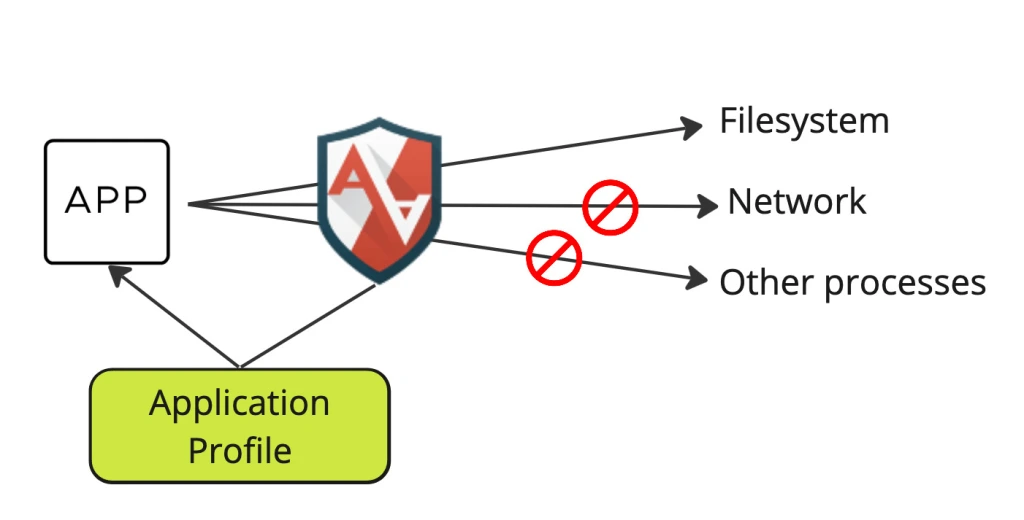
What is AppArmor??
AppArmor is an effective and easy-to-use Linux application security system. AppArmor proactively protects the operating system and applications from external or internal threats, even zero-day attacks, by enforcing good behavior and preventing both known and unknown application flaws from being exploited.
|
|
Enough theory - let’s try to understand what AppArmor did here from the logs.
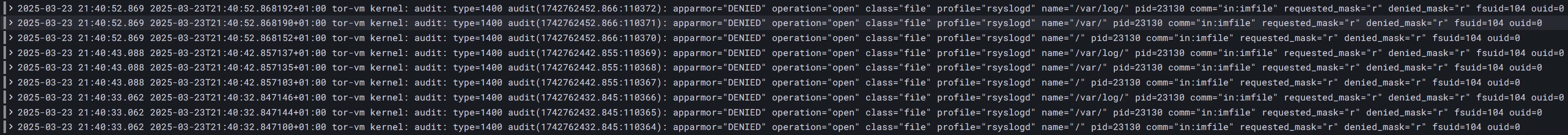
AppArmor DENIED an operation performed by the rsyslogd process (PID 23130) running under the “tor-vm” job. The process, identified as “in:imfile”, attempted to open and read (/var/log/) with read permissions, but was blocked by AppArmor
. This denial occurred because the AppArmor profile for rsyslogd does not allow this specific access.
The details of the denied operation are as follows:
- Operation: open (attempting to open a file)
- Requested mask: r (read permission)
- Denied mask: r (read permission was denied)
- Name: /var/log/ (the directory that was attempted to be accessed)
- Profile: rsyslogd (the AppArmor profile that enforced this restriction)
This log entry demonstrates how AppArmor is actively preventing potentially unauthorized access to system resources, even by system processes like rsyslogd . Such restrictions help maintain system security by ensuring that processes only access resources they are explicitly allowed to, reducing the potential impact of security vulnerabilities or misconfigurations.
How to fix the issue with access to logs in /var/log ?
We need to edit /etc/apparmor.d/local/usr.sbin.rsyslogd file and add following entries:
|
|
Once done we need apply the changes by executing following command sudo apparmor_parser -r -W -T /etc/apparmor.d/usr.sbin.rsyslogd.
Summary
By doing that we allow logs to be read by other processes. Here is Ubuntu Bug which might give you some more details.